List of Tables
Table 1. Global Data Security Market Size Growth Rate by Type, 2020 VS 2024 VS 2031 (US$ Million)
Table 2. Global Data Security Market Size Growth Rate by Application, 2020 VS 2024 VS 2031 (US$ Million)
Table 3. Global Data Security Revenue Grow Rate (CAGR) by Region: 2020 VS 2024 VS 2031 (US$ Million)
Table 4. Global Data Security Revenue by Region (2020-2025) & (US$ Million)
Table 5. Global Data Security Revenue by Region (2026-2031) & (US$ Million)
Table 6. Emerging Market Revenue Grow Rate (CAGR) by Country (2020 VS 2024 VS 2031) (US$ Million)
Table 7. Global Data Security Revenue by Players (2020-2025) & (US$ Million)
Table 8. Global Data Security Revenue Market Share by Players (2020-2025)
Table 9. Global Key Players’Ranking Shift (2023 vs. 2024) (Based on Revenue)
Table 10. Global Data Security by Player Tier (Tier 1, Tier 2, and Tier 3) & (based on the Revenue in Data Security as of 2024)
Table 11. Global Data Security Average Gross Margin (%) by Player (2020 VS 2024)
Table 12. Global Data Security Companies Headquarters
Table 13. Global Data Security Market Concentration Ratio (CR5 and HHI)
Table 14. Key Market Entrant/Exit (2020-2024) – Drivers & Impact Analysis
Table 15. Key Mergers & Acquisitions, Expansion Plans, R&D Investment
Table 16. Global Data Security Revenue by Type (2020-2025) & (US$ Million)
Table 17. Global Data Security Revenue by Type (2026-2031) & (US$ Million)
Table 18. Key Product Attributes and Differentiation
Table 19. Global Data Security Revenue by Application (2020-2025) & (US$ Million)
Table 20. Global Data Security Revenue by Application (2026-2031) & (US$ Million)
Table 21. Data Security High-Growth Sectors Demand CAGR (2024-2031)
Table 22. Top Customers by Region
Table 23. Top Customers by Application
Table 24. North America Data Security Growth Accelerators and Market Barriers
Table 25. North America Data Security Revenue Grow Rate (CAGR) by Country (2020 VS 2024 VS 2031) (US$ Million)
Table 26. Europe Data Security Growth Accelerators and Market Barriers
Table 27. Europe Data Security Revenue Grow Rate (CAGR) by Country: 2020 VS 2024 VS 2031 (US$ Million)
Table 28. Asia-Pacific Data Security Growth Accelerators and Market Barriers
Table 29. Asia-Pacific Data Security Revenue Grow Rate (CAGR) by Region: 2020 VS 2024 VS 2031 (US$ Million)
Table 30. Central and South America Data Security Investment Opportunities and Key Challenges
Table 31. Central and South America Data Security Revenue Grow Rate (CAGR) by Country (2020 VS 2024 VS 2031) (US$ Million)
Table 32. Middle East and Africa Data Security Investment Opportunities and Key Challenges
Table 33. Middle East and Africa Data Security Revenue Grow Rate (CAGR) by Country (2020 VS 2024 VS 2031) (US$ Million)
Table 34. Broadcom (Symantec) Corporation Information
Table 35. Broadcom (Symantec) Description and Major Businesses
Table 36. Broadcom (Symantec) Product Features and Attributes
Table 37. Broadcom (Symantec) Revenue (US$ Million) and Gross Margin (2020-2025)
Table 38. Broadcom (Symantec) Revenue Proportion by Product in 2024
Table 39. Broadcom (Symantec) Revenue Proportion by Application in 2024
Table 40. Broadcom (Symantec) Revenue Proportion by Geographic Area in 2024
Table 41. Broadcom (Symantec) Data Security SWOT Analysis
Table 42. Broadcom (Symantec) Recent Developments
Table 43. Check Point Corporation Information
Table 44. Check Point Description and Major Businesses
Table 45. Check Point Product Features and Attributes
Table 46. Check Point Revenue (US$ Million) and Gross Margin (2020-2025)
Table 47. Check Point Revenue Proportion by Product in 2024
Table 48. Check Point Revenue Proportion by Application in 2024
Table 49. Check Point Revenue Proportion by Geographic Area in 2024
Table 50. Check Point Data Security SWOT Analysis
Table 51. Check Point Recent Developments
Table 52. Cisco Corporation Information
Table 53. Cisco Description and Major Businesses
Table 54. Cisco Product Features and Attributes
Table 55. Cisco Revenue (US$ Million) and Gross Margin (2020-2025)
Table 56. Cisco Revenue Proportion by Product in 2024
Table 57. Cisco Revenue Proportion by Application in 2024
Table 58. Cisco Revenue Proportion by Geographic Area in 2024
Table 59. Cisco Data Security SWOT Analysis
Table 60. Cisco Recent Developments
Table 61. CyberArk Corporation Information
Table 62. CyberArk Description and Major Businesses
Table 63. CyberArk Product Features and Attributes
Table 64. CyberArk Revenue (US$ Million) and Gross Margin (2020-2025)
Table 65. CyberArk Revenue Proportion by Product in 2024
Table 66. CyberArk Revenue Proportion by Application in 2024
Table 67. CyberArk Revenue Proportion by Geographic Area in 2024
Table 68. CyberArk Data Security SWOT Analysis
Table 69. CyberArk Recent Developments
Table 70. Elektrobit Corporation Information
Table 71. Elektrobit Description and Major Businesses
Table 72. Elektrobit Product Features and Attributes
Table 73. Elektrobit Revenue (US$ Million) and Gross Margin (2020-2025)
Table 74. Elektrobit Revenue Proportion by Product in 2024
Table 75. Elektrobit Revenue Proportion by Application in 2024
Table 76. Elektrobit Revenue Proportion by Geographic Area in 2024
Table 77. Elektrobit Data Security SWOT Analysis
Table 78. Elektrobit Recent Developments
Table 79. Fortinet Corporation Information
Table 80. Fortinet Description and Major Businesses
Table 81. Fortinet Product Features and Attributes
Table 82. Fortinet Revenue (US$ Million) and Gross Margin (2020-2025)
Table 83. Fortinet Recent Developments
Table 84. HAAS Alert Corporation Information
Table 85. HAAS Alert Description and Major Businesses
Table 86. HAAS Alert Product Features and Attributes
Table 87. HAAS Alert Revenue (US$ Million) and Gross Margin (2020-2025)
Table 88. HAAS Alert Recent Developments
Table 89. Harman Corporation Information
Table 90. Harman Description and Major Businesses
Table 91. Harman Product Features and Attributes
Table 92. Harman Revenue (US$ Million) and Gross Margin (2020-2025)
Table 93. Harman Recent Developments
Table 94. IBM Corporation Information
Table 95. IBM Description and Major Businesses
Table 96. IBM Product Features and Attributes
Table 97. IBM Revenue (US$ Million) and Gross Margin (2020-2025)
Table 98. IBM Recent Developments
Table 99. Infineon Technologies Corporation Information
Table 100. Infineon Technologies Description and Major Businesses
Table 101. Infineon Technologies Product Features and Attributes
Table 102. Infineon Technologies Revenue (US$ Million) and Gross Margin (2020-2025)
Table 103. Infineon Technologies Recent Developments
Table 104. Karamba Security Corporation Information
Table 105. Karamba Security Description and Major Businesses
Table 106. Karamba Security Product Features and Attributes
Table 107. Karamba Security Revenue (US$ Million) and Gross Margin (2020-2025)
Table 108. Karamba Security Recent Developments
Table 109. McAfee Corporation Information
Table 110. McAfee Description and Major Businesses
Table 111. McAfee Product Features and Attributes
Table 112. McAfee Revenue (US$ Million) and Gross Margin (2020-2025)
Table 113. McAfee Recent Developments
Table 114. NSFOCUS Corporation Information
Table 115. NSFOCUS Description and Major Businesses
Table 116. NSFOCUS Product Features and Attributes
Table 117. NSFOCUS Revenue (US$ Million) and Gross Margin (2020-2025)
Table 118. NSFOCUS Recent Developments
Table 119. Palo Alto Networks Corporation Information
Table 120. Palo Alto Networks Description and Major Businesses
Table 121. Palo Alto Networks Product Features and Attributes
Table 122. Palo Alto Networks Revenue (US$ Million) and Gross Margin (2020-2025)
Table 123. Palo Alto Networks Recent Developments
Table 124. QI-ANXIN Corporation Information
Table 125. QI-ANXIN Description and Major Businesses
Table 126. QI-ANXIN Product Features and Attributes
Table 127. QI-ANXIN Revenue (US$ Million) and Gross Margin (2020-2025)
Table 128. QI-ANXIN Recent Developments
Table 129. Qualcomm Corporation Information
Table 130. Qualcomm Description and Major Businesses
Table 131. Qualcomm Product Features and Attributes
Table 132. Qualcomm Revenue (US$ Million) and Gross Margin (2020-2025)
Table 133. Qualcomm Recent Developments
Table 134. Rapid7 Corporation Information
Table 135. Rapid7 Description and Major Businesses
Table 136. Rapid7 Product Features and Attributes
Table 137. Rapid7 Revenue (US$ Million) and Gross Margin (2020-2025)
Table 138. Rapid7 Recent Developments
Table 139. RSA Security Corporation Information
Table 140. RSA Security Description and Major Businesses
Table 141. RSA Security Product Features and Attributes
Table 142. RSA Security Revenue (US$ Million) and Gross Margin (2020-2025)
Table 143. RSA Security Recent Developments
Table 144. Sangfor Technologies Corporation Information
Table 145. Sangfor Technologies Description and Major Businesses
Table 146. Sangfor Technologies Product Features and Attributes
Table 147. Sangfor Technologies Revenue (US$ Million) and Gross Margin (2020-2025)
Table 148. Sangfor Technologies Recent Developments
Table 149. Thales Corporation Information
Table 150. Thales Description and Major Businesses
Table 151. Thales Product Features and Attributes
Table 152. Thales Revenue (US$ Million) and Gross Margin (2020-2025)
Table 153. Thales Recent Developments
Table 154. TOPSEC Corporation Information
Table 155. TOPSEC Description and Major Businesses
Table 156. TOPSEC Product Features and Attributes
Table 157. TOPSEC Revenue (US$ Million) and Gross Margin (2020-2025)
Table 158. TOPSEC Recent Developments
Table 159. Trend Micro Corporation Information
Table 160. Trend Micro Description and Major Businesses
Table 161. Trend Micro Product Features and Attributes
Table 162. Trend Micro Revenue (US$ Million) and Gross Margin (2020-2025)
Table 163. Trend Micro Recent Developments
Table 164. Venustech Corporation Information
Table 165. Venustech Description and Major Businesses
Table 166. Venustech Product Features and Attributes
Table 167. Venustech Revenue (US$ Million) and Gross Margin (2020-2025)
Table 168. Venustech Recent Developments
Table 169. Raw Materials Key Suppliers
Table 170. Distributors List
Table 171. Market Trends and Market Evolution
Table 172. Market Drivers and Opportunities
Table 173. Market Challenges, Risks, and Restraints
Table 174. Research Programs/Design for This Report
Table 175. Key Data Information from Secondary Sources
Table 176. Key Data Information from Primary Sources
List of Figures
Figure 1. Data Security Product Picture
Figure 2. Global Data Security Market Size Growth Rate by Type, 2020 VS 2024 VS 2031 (US$ Million)
Figure 3. Software Product Picture
Figure 4. Hardware Product Picture
Figure 5. Global Data Security Market Size Growth Rate by Application, 2020 VS 2024 VS 2031 (US$ Million)
Figure 6. BFSI
Figure 7. IT & Telecom
Figure 8. Manufacturing
Figure 9. Automobile
Figure 10. Others
Figure 11. Data Security Report Years Considered
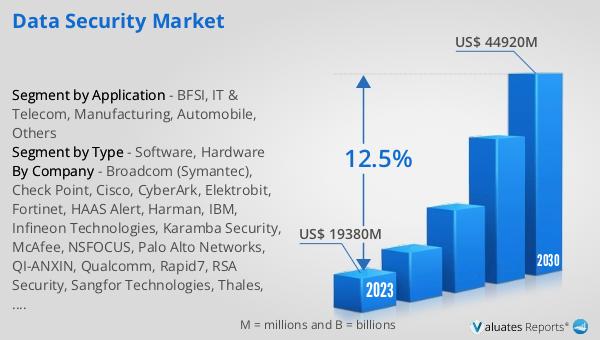
Figure 12. Global Data Security Revenue, (US$ Million), 2020 VS 2024 VS 2031
Figure 13. Global Data Security Revenue (2020-2031) & (US$ Million)
Figure 14. Global Data Security Revenue (CAGR) by Region: 2020 VS 2024 VS 2031 (US$ Million)
Figure 15. Global Data Security Revenue Market Share by Region (2020-2031)
Figure 16. Global Data Security Revenue Market Share Ranking (2024)
Figure 17. Tier Distribution by Revenue Contribution (2020 VS 2024)
Figure 18. Software Revenue Market Share by Player in 2024
Figure 19. Hardware Revenue Market Share by Player in 2024
Figure 20. Global Data Security Revenue Market Share by Type (2020-2031)
Figure 21. Global Data Security Revenue Market Share by Application (2020-2031)
Figure 22. North America Data Security Revenue YoY (2020-2031) & (US$ Million)
Figure 23. North America Top 5 Players Data Security Revenue (US$ Million) in 2024
Figure 24. North America Data Security Revenue (US$ Million) by Type (2020 - 2031)
Figure 25. North America Data Security Revenue (US$ Million) by Application (2020-2031)
Figure 26. US Data Security Revenue (2020-2031) & (US$ Million)
Figure 27. Canada Data Security Revenue (2020-2031) & (US$ Million)
Figure 28. Mexico Data Security Revenue (2020-2031) & (US$ Million)
Figure 29. Europe Data Security Revenue YoY (2020-2031) & (US$ Million)
Figure 30. Europe Top 5 Players Data Security Revenue (US$ Million) in 2024
Figure 31. Europe Data Security Revenue (US$ Million) by Type (2020-2031)
Figure 32. Europe Data Security Revenue (US$ Million) by Application (2020-2031)
Figure 33. Germany Data Security Revenue (2020-2031) & (US$ Million)
Figure 34. France Data Security Revenue (2020-2031) & (US$ Million)
Figure 35. U.K. Data Security Revenue (2020-2031) & (US$ Million)
Figure 36. Italy Data Security Revenue (2020-2031) & (US$ Million)
Figure 37. Russia Data Security Revenue (2020-2031) & (US$ Million)
Figure 38. Asia-Pacific Data Security Revenue YoY (2020-2031) & (US$ Million)
Figure 39. Asia-Pacific Top 8 Players Data Security Revenue (US$ Million) in 2024
Figure 40. Asia-Pacific Data Security Revenue (US$ Million) by Type (2020-2031)
Figure 41. Asia-Pacific Data Security Revenue (US$ Million) by Application (2020-2031)
Figure 42. Indonesia Data Security Revenue (2020-2031) & (US$ Million)
Figure 43. Japan Data Security Revenue (2020-2031) & (US$ Million)
Figure 44. South Korea Data Security Revenue (2020-2031) & (US$ Million)
Figure 45. Australia Data Security Revenue (2020-2031) & (US$ Million)
Figure 46. India Data Security Revenue (2020-2031) & (US$ Million)
Figure 47. Indonesia Data Security Revenue (2020-2031) & (US$ Million)
Figure 48. Vietnam Data Security Revenue (2020-2031) & (US$ Million)
Figure 49. Malaysia Data Security Revenue (2020-2031) & (US$ Million)
Figure 50. Philippines Data Security Revenue (2020-2031) & (US$ Million)
Figure 51. Singapore Data Security Revenue (2020-2031) & (US$ Million)
Figure 52. Central and South America Data Security Revenue YoY (2020-2031) & (US$ Million)
Figure 53. Central and South America Top 5 Players Data Security Revenue (US$ Million) in 2024
Figure 54. Central and South America Data Security Revenue (US$ Million) by Type (2020-2031)
Figure 55. Central and South America Data Security Revenue (US$ Million) by Application (2020-2031)
Figure 56. Brazil Data Security Revenue (2020-2025) & (US$ Million)
Figure 57. Argentina Data Security Revenue (2020-2025) & (US$ Million)
Figure 58. Middle East and Africa Data Security Revenue YoY (2020-2031) & (US$ Million)
Figure 59. Middle East and Africa Top 5 Players Data Security Revenue (US$ Million) in 2024
Figure 60. South America Data Security Revenue (US$ Million) by Type (2020-2031)
Figure 61. Middle East and Africa Data Security Revenue (US$ Million) by Application (2020-2031)
Figure 62. GCC Countries Data Security Revenue (2020-2025) & (US$ Million)
Figure 63. Israel Data Security Revenue (2020-2025) & (US$ Million)
Figure 64. Egypt Data Security Revenue (2020-2025) & (US$ Million)
Figure 65. South Africa Data Security Revenue (2020-2025) & (US$ Million)
Figure 66. Data Security Industry Chain Mapping
Figure 67. Channels of Distribution (Direct Vs Distribution)
Figure 68. Bottom-up and Top-down Approaches for This Report
Figure 69. Data Triangulation
Figure 70. Key Executives Interviewed